Do I need to invest in malware antivirus protection?
Malware threatens business on a global persistent scale. In a recent study, the UK ranked 4th with ransomware detections. Nearly 30 billion Pounds lost due to cyber attacks in business processing. Over 32% of businesses and 22% of Charities had cyber breaches. This is actually a crisis waiting to happen for all of us.
These unexpected security breaches will hit company revenue and cyber analyst consultancy is on fire right now. Yet common thinking is that only large organisations are prime focus for malware attacks. Therefore you may ask, why does my small to medium sized business need antivirus and malware protection? You need malware antivirus protection because the real victim is small business. Security breaches mean data and communication loss, crashed system functions, exposed customer details and loss of reputation, and reduced revenue.

Small businesses are the easy targets of the hackers. The hackers can hit more than a hundred small businesses at a time instead of intruding into a large organisation.
The UK Department for Digital, Culture, Media and Support published the following
In businesses that had these kinds of negative outcomes, the average (mean) cost to the business was £4,180 in 2019. This is higher than in 2018 (£3,160) and 2017 (£2,450). It indicates a broad trend of rising costs in cases where cyber attacks are able to penetrate an organisations defences.
Once again, the average costs faced by larger businesses in these cases tend to be much higher (£9,270 for medium firms and £22,700 for large firms in 2019). And for charities facing such negative outcomes from breaches, the average cost was £9,470 in 2019.
However, the indirect costs, long-term costs and intangible costs of breaches – things like lost productivity or reputational damage – tend to be overlooked. This means that, when organisations reflect on their approaches to cyber security, they may be undervaluing the true cost and impact of cyber security breaches.
You may be one of those larger firms handling large sums without implementing high-end security technology in your transaction systems. Another UK study revealed that Malware threatens businesses with less than 500 employees had lost £1.8M per attack. The cyber breach drains out the sum and reputation of the company quickly. Even those you would expect to have malware antivirus, i.e.Travelex – had to pay out $2.3M to retrieve lost information this year.
What are the cyber security threats for my business?
We’ve listed several Malware security threats for your business processing. It is high time for any company owner to get a clear picture of these attacks to enhance the security systems on their transaction platforms.
The general security threats you should be aware of:
Malware Attacks
The Malware attack is one of the cyber attacks common to small business. This attack occurs due to the Trojan and virus codes created by hackers to damage the data and intrude into networks. This type of attack enters into to the business IT systems through a malicious software download, unauthorised web page, spam email, or a connection with an infected system.
Employees of small enterprises use their personal computers or persoal emails to complete the odd task. This type of work culture results in malware attacks, which change DNS settings, re-directing users’ traffic through malware servers. Most personal computers are highly prone to malware infections.
Phishing Attacks
The Phishing attack is a widely spread cyber attack in small firms. It brings a complete breach of crucial data, the cyber criminal gains access to nearly 90% of business data in no time. This type of attack occurs through fake cloned sites or emails pretending to be real, requesting sensitive data to be entered in. Once employees open within the work email, the entire system will be unwrapped.
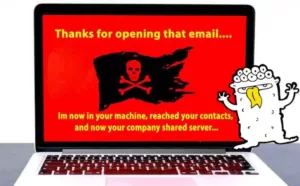
Ransomware
The next well-known cyberattack that prevails commonly among firms is Ransomware. In this kind of attack, the hackers will lock the organization’s data and force the victims to pay. The intruders unlock the data after receiving a ransom from the victims. The hackers target small firms because they are aware that there is no proper technology to back up crucial data.
What are the risks
if I get a malware attack?
The dangers related to malware cyber-attacks in business communication systems are as follows.
Data loss
Cyber attacks will unlock data access and damage the data. The virus targets the database and establishes complete control of the firm’s data in no time. Imagine losing all customer details and your entire lead generation to date.
Interferes with business communication
The hackers attack the business email channel, thereby leading to complete damage. A malicious link steps into the organisation’s email platform triggering the employees to download the virus into their network of electronic devices with now virus’s on Andriod and iPhones + laptops.
Reduction of business revenue
Due to Ransom attacks, the victims have to pay a large sum to unlock their important data from the hackers. It will ultimately affect the profits of that financial year. The ransom attacks marked the end of fewer small organisations worldwide.
The Reputation of your Company
After a malware attack, small businesses face tough challenges to rebuild their reputation amidst the competitive environment. Cyberattacks affect the optimum functioning of the organisation in the future. Worst case the firm’s entire revenue and profit system can collapse due to 1) fines for customer data loss, 2) loss of cash flow from a pause in trading, and 3) an urgent investment in the right antivirus protection.
Crashes your entire system functions
When malware strikes a computer in an organisation, automatically the entire systems shut down in a fraction of a second. It causes complete damage to the electronic devices in a firm. An entrepreneur could be looking for technically skilled people to repair the damaged computers.
Interrupts the normal workflow
Due to malicious attack, the firm faces interruption from their normal workflow. It will reflect on the profit reports on that financial year. The firm has to strive hard to resume its business processing after the virus attack. It takes nearly a year to compensate for the loss due to the suspicious activities of the hackers. The repair cost after the attack seems to be devastating and some newbie entrepreneurs disappear from the competitive market.
How can a malware virus
impact my Cloud System?
Harnessing Cloud platforms enables you to scale your business beyond its physical hardware size. This evolution in scaleable infrastructure opens the door to configuration issues and ultimately malware threats on your business. A security risk on this Cloud system can bring drastic consequences. The hackers inject the spyware into the cloud storage of a firm and eavesdrop on the organisation’s data. The firm’s employees work on this cloud platform without this knowledge and the hacker will silently steal the data at one point in time without anyone knowing.

In the Cloud systems, data wipe is a common issue when there is an improper collaboration with the service providers. IT managers should review the terms and conditions of the cloud storage provider before signing into their services. Ensure the service providers have ample features to restrict anonymous entry into the storage area to avoid a data breach.
One of the downfalls following a virus attack is the deactivation of your presence in the digital market. The data related to your company will be with-held preventing you from reaching the target customers. The owners will lose their business operation if these circumstances prevail in the long run.
Another interesting one is the ‘Man-in-Cloud –Attack’. It’s a recent security threat under cloud storage systems. In this type of attack, the intruder hijacks the user account details easily by cloning the sync token used by the user. This is basically a saved file which stores the user’s login details, so they don’t have to continuously log in. The data in the cloud storage are relatively vulnerable and they are highly prone to hacking. A similar scenario occurred with Amazon and Google.
Who invites the computer virus inside my business?
The sources of Malware attacks are closer than you think.
Employees invite malware virus’s unintentionally
The Employees small-scale businesses are unaware of the Malware attacks. They do not know how to set strong passwords while working on cloud storage systems. The employees lack skills in detecting suspicious activities on their working network. Most of them are ignorant about cyber attacks.
If when travelling employees might use the public Wi-Fi network to access their firm’s portfolio without knowing the hidden dangers. The personal computers of the employees can easily have infections, which intrude into the company’s network in no time.
Solution: Firms should offer regular seminars on recent cyber attacks for their employees. Training is necessary to educate the employees in assigning strong passwords and optimum ways to handle crucial data on cloud storage.
Create a department or point person in your firm with the title ‘Cyber Security Category Leader’ to overlook the proper functioning of the firm’s communication and transaction channel. The technical expert in this team should identify and eradicate the suspicious moves on the channel before the circumstance becomes worse.
Competitors can be behind the virus.
Cyberattacks can be initiated by competitors, especially those overseas who look at you as a threat or they wish to benchmark you in their own territory. Attacks like this are common because this is a fast way to gain knowledge on cost prices, price lists, suppliers, prototype designs, marketing plans, or next season’s year’s product launch.
Solution: Young entrepreneurs should implement security gateways to protect their small business activities from the interference of hackers. It is highly advisable to embed Email Security Gateways to protect the company documents and conversations. To overcome malware attacks you can go for ‘Endpoint Protection’ and ‘Web Security’.
Hacking for Money
Professional hackers target small firms with limited employees. These hackers learn recent techniques to crash the security systems of your firm and earn money in no time. Most hackers inject ransomware into the system to hijack data for money.

Solution: Endpoint Detection and Response is one of the reliable security techniques to get rid of ransomware issues. Business owners must always look for recent cyber threats and acquire knowledge to implement relevant security measures on their network.
Effective measures to prevent Malware attack
Latest Security Techniques
As you all know, hackers don’t use older hacking methods to intrude, instead they figure out exciting methods to interfere with the business processes. From the hacker’s perspective, they will implement a new form of viral attack on the company’s network to stumble the smooth functioning of the enterprise. It is high time for your business to take proactive steps to get rid of the hacking methodologies. You can go to ‘Endpoint Protection’, ‘Web Security’, and ‘Email Security Gateways’ etc. All these modules protect the data from hacking thereby providing security grounds to overcome malware attack issues.
Educate the Employee
Business must contribute to training the employees about the cybersecurity system. Security awareness training brings tremendous changes in the employee attitude while handling vulnerable data related to the organisation. The professionals from cybersecurity should address the employees periodically to update their skills related to data protection.
Organise or limit the access
Only the admins and authorised employees should connect with the iCloud environment to work with the stored data. The firm can establish a Cloud Lock technology to accomplish complete control over it. The entrepreneurs must formulate rules and regulations to work on the computer components on the office premises. This can include denial of access to unauthorised web pages, request permission to enable or download any tool from the online platform, prohibit the entry of unnecessary pop-ups carrying malware, etc.
Effective systems backup
To overcome the consequence of ransomware attack it is highly recommended to backup all the crucial data on various forms for later retrieval. All businesses should not hesitate to spend on sophisticated backup technology to shelter against cyber attack. Backed up data is one of the proactive actions against virus attacks.
Password Management
Owners should maintain the passwords personally without any leaks. If you can manage the passwords on your own then you are free from inside threats within the business. There are chances for the employee to become ‘black sheep’ stealing data to serve your competitors. You can establish a well-structured password management system to modify and update the characters efficiently after regular intervals.
Conclusion – the pitch part.
Cyber-attacks have become a great threat to small-scale enterprises. It is the perfect time to acquire awareness about cybersecurity and implement it right now.
We at Cream Soda have business partnerships with scaleable global cybersecurity organisations, who can reduce the scope and cost to suit any business size.
In relation to Cloud Security we can provide you the ability to
- Track devices and applications on the network.
- Identity unpatched applications and op systems.
- See real-time and historical visibility.
- Monitor data usage and user activity.
- Detect unwanted and vulnerable applications.
- Fix unprotected and rogue systems.
- Stop admin account abuse.
- Satisfy compliance requirements.
- Eliminate malware cyber threats on your business.
Go for a reliable antivirus business program, not family / soft orientated Nortons or Kaspersky, to protect your data from security threats. Educate, and empower your employees to be aware. Training programs for employees, and installing the latest Malware cybersecurity technologies are an effective strategy to fight malware attacks and maintain financial cash flow – your working capital.
CONTACT US
Email: support@creamsodamedia.com | Tel: 01276 490448